6.3 Configuring Linux Wireless Security
In this section we will go through the steps involved in configuring a
Linux system to operate on an encrypted WiFi wireless network. This is
either a one or two step process depending on whether you already have
an encrypted network to which you are adding a Linux system or whether
you also need to configure your existing wireless network to use
encyption.
6.3.1 Configuring the Wireless Base Station
If you have already followed the instruction in the user guide that
came with your wireless base station to configure the network to use
WEP encryption you can skip this step and move on to the next section.
If you have not done so then the first thing to do is read the wireless
base station user guide to find out how to configure the security
features of the device. Such devices typically have a web interface
that you can access from your web browser. The documentation will tell
you the IP address to enter and this topic is covered in
Chapter 2.
A typical web based configuration screen is shown if Figure 6.3 below.
In this example a 128-bit encryption key has been entered.
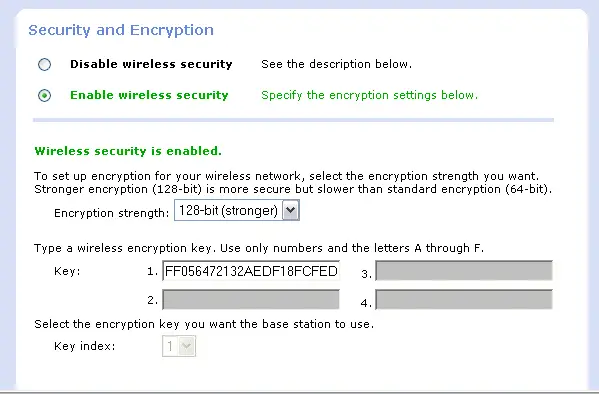
Figure 6.3 - A typical wireless base station secuirty configuration
screen
For 64-bit encryption enter a 10 digit hexadecimal key and for 128-bit
encryption enter a 26 digit hexadecimal key. Details of encryption and
keys can be found in
Section 6.1.
