Solaris Management Console Tools
The Solaris Management Console provides access to toolboxes of GUI-based administration tools. These
tools enable you to edit items in various configuration databases. In Trusted
Extensions, the Solaris Management Console is the administrative interface for users, roles, and
the trusted network databases.
Trusted Extensions extends the Solaris Management Console:
Solaris Management Console tools are collected into toolboxes according to scope and security
policy. To administer Trusted Extensions, Trusted Extensions provides toolboxes whose Policy=TSOL. You can
access tools according to scope, that is, according to naming service. The available
scopes are local host and LDAP.
The Solaris Management Console is shown in the following figure. A Scope=Files
Trusted Extensions toolbox is loaded, and the Users tool set is open.
Figure 8-3 Typical Trusted Extensions Toolbox in the Solaris Management Console
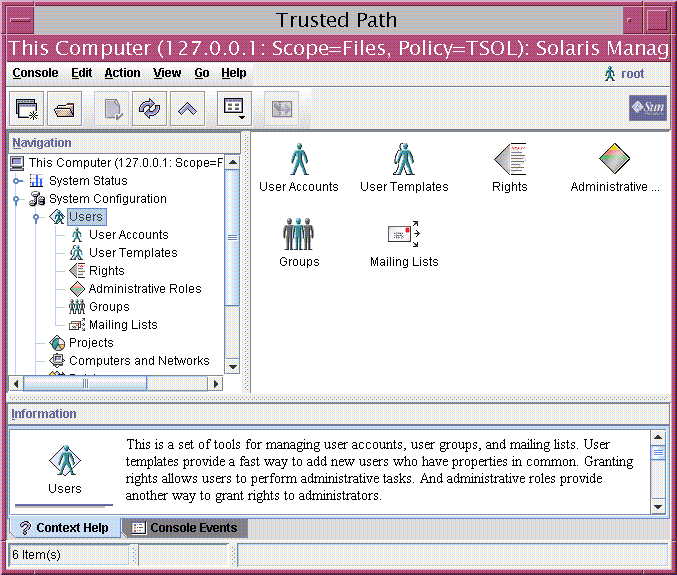
Trusted Extensions Tools in the Solaris Management Console
Trusted Extensions adds configurable security attributes to three tools:
User Accounts tool – Is the administrative interface to change a user's label, change a user's view of labels, and to control account usage.
Administrative Roles tool – Is the administrative interface to change a role's label range and screen-locking behavior when idle.
Rights tool – Includes CDE actions that can be assigned to rights profiles. Security attributes can be assigned to these actions.
Trusted Extensions adds two tools to the Computers and Networks tool set:
Security Templates tool – Is the administrative interface for managing the label aspects of hosts and networks. This tool modifies the tnrhtp and tnrhdb databases, enforces syntactic accuracy, and updates the kernel with the changes.
Trusted Network Zones tool – Is the administrative interface for managing the label aspects of zones. This tool modifies the tnzonecfg database, enforces syntactic accuracy, and updates the kernel with the changes.
Figure 8-4 shows the Files toolbox with the Computers and Networks tool set highlighted.
The Trusted Extensions tools appear below the tool set.
Figure 8-4 Computers and Networks Tool Set in the Solaris Management Console
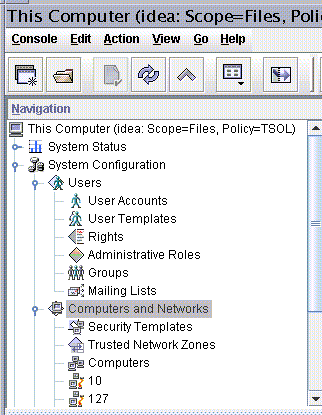
Security Templates Tool
A security template describes a set of security attributes that can be assigned to
a group of hosts. The Security Templates tool enables you to conveniently assign
a specific combination of security attributes to a group of hosts. These attributes
control how data is packaged, transmitted, and interpreted. Hosts that are assigned to
a template have identical security settings.
The hosts are defined in the Computers tool. The security attributes of the
hosts are assigned in the Security Templates tool. The Modify Template dialog box
contains two tabs:
General tab – Describes the template. Includes its name, host type, default label, domain of interpretation (DOI), accreditation range, and set of discrete sensitivity labels.
Hosts Assigned to Template tab – Lists all the hosts on the network that you have assigned to this template.
Trusted networking and security templates are explained in more detail in Chapter 18, Trusted Networking (Overview).
Trusted Network Zones Tool
The Trusted Network Zones tool identifies the zones on your system. Initially, the
global zone is listed. When you add zones and their labels, the zone
names display in the pane. Zone creation usually occurs during system configuration. Label
assignment, multilevel port configuration, and label policy is configured in this tool. For
details, see Chapter 16, Managing Zones in Trusted Extensions (Tasks).
Client-Server Communication With the Solaris Management Console
Typically, a Solaris Management Console client administers systems remotely. On a network
that uses LDAP as a naming service, a Solaris Management Console client
connects to the Solaris Management Console server that runs on the LDAP server.
The following figure shows this configuration.
Figure 8-5 Solaris Management Console Client Using an LDAP Server to Administer the Network
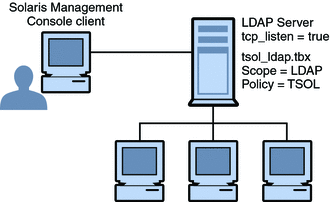
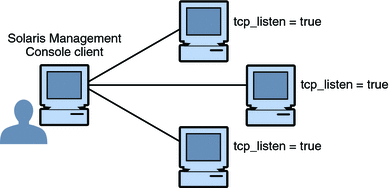
Figure 8-6 shows a network that is not configured with an LDAP server. The
administrator configured each remote system with a Solaris Management Console server.
Figure 8-6 Solaris Management Console Client Administering Individual Remote Systems on a Network
Solaris Management Console Documentation
The main source of documentation for the Solaris Management Console is its
online help. Context-sensitive help is tied to the currently selected feature and is
displayed in the information pane. Expanded help topics are available from the Help
menu or by clicking links in the context-sensitive help. Further information is provided
in Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration. Also see Using the Solaris Management Tools With RBAC (Task Map) in System Administration Guide: Basic Administration.
