Virtual Private Networks and IPsec
A configured tunnel is a point-to-point interface. The tunnel enables one IP packet
to be encapsulated within another IP packet. A correctly configured tunnel requires both
a tunnel source and a tunnel destination. For more information, see the tun(7M)
man page and Configuring Tunnels for IPv6 Support.
A tunnel creates an apparent physical interface to IP. The physical link's integrity
depends on the underlying security protocols. If you set up the security associations
(SAs) securely, then you can trust the tunnel. Packets that exit the tunnel
must have originated from the peer that was specified in the tunnel destination.
If this trust exists, you can use per-interface IP forwarding to create a
virtual private network (VPN).
You can use IPsec to construct a VPN. IPsec secures the connection. For
example, an organization that uses VPN technology to connect offices with separate networks
can deploy IPsec to secure traffic between the two offices.
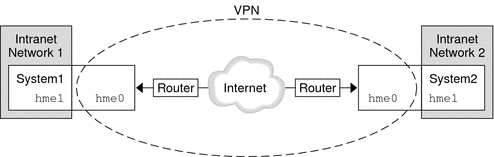
The following figure illustrates how two offices use the Internet to form their
VPN with IPsec deployed on their network systems.
Figure 19-7 Virtual Private Network
For a detailed example of the setup procedure, see How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv4. For IPv6
networks, see How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv6.
